
Van Flowers, Senior Systems Engineer, Cloudian

VMware Cloud Service Providers Can Expand Their Business with Ransomware Protection
VMware Cloud Service Providers (VCSPs) have emerged as an excellent alternative to hyperscalers for organizations that want to store their data in the cloud. By employing object storage, such as Cloudian HyperStore, these service providers can deliver hyperscaler-like scalability and flexibility while addressing organizations’ individual performance, data sovereignty, budget and security needs. Data security has become especially important due to the proliferation of ransomware attacks over the past few years, and VCSPs that can help their customers protect their data against this threat can expand their business by growing their footprint with existing clients and attracting new ones.
The best way to protect data against ransomware is with data immutability using Object Lock technology. As perimeter security solutions increasingly prove ineffective in preventing ransomware from getting in, having an immutable data backup copy ensures that this data cannot be deleted or encrypted. In the event of a ransomware attack, organizations can easily recover the unchanged backup without having to pay ransom.
Object Lock can be implemented as part of an automated backup workflow. For example, VCSPs using Veeam, Rubrik or Commvault can deploy Cloudian’s S3 Object Lock to seamlessly integrate a ransomware-proof, immutable S3 bucket into their customer backup solution.
So how do you do it? As shown in the screen shot below, all that’s needed to create the immutable bucket is to tick the slider, and you’re in the ransomware protection business! This simple task is performed at the time the bucket is created, and once created, the data written into the bucket cannot be deleted, altered or changed in any way until the defined immutability period expires. The bad guys – even a rogue administrator – can’t change it, but restores can be done in a flash!
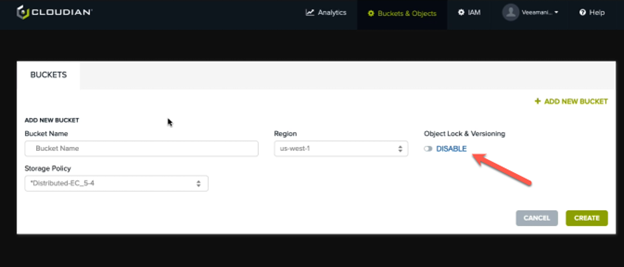
Ransomware attacks are growing by the thousands every day, and VCSPs’ ability to offer this vital protection to their customers data can be a key contributor to continued growth, and to their customers’ peace of mind.
VCSPs – don’t let another minute go by without having immutable storage available for your customers. Nothing is easier to configure, integrate and fortify your customers’ data security than immutable storage built on Cloudian. Contact your local Cloudian representative for more information or drop me a note (vflowers@cloudian.com) or a tweet (@avf925). I’m always happy to help!
And to learn more about Cloudian solutions for VCSPs, visit Object Storage for VMware Cloud Director | Cloudian.



 Grant Jacobson, Director of Technology Alliances and Partner Marketing, Cloudian
Grant Jacobson, Director of Technology Alliances and Partner Marketing, Cloudian